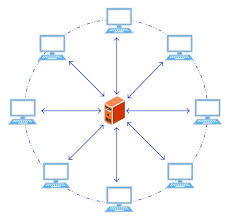
About Us
MNTech Enterprises Private Limited (MEPL) is an incorporated company in India to provide "Cyber Security Solution" and cater industries with some unique and comprehensive software. MEPL serve industries as SaaS with Cyber Security products includes End Point Solution, Boot Level Encryption, Disk Encryption, Monitoring, Tracking, and prevention from Data Leak.
Proactive Security
Every day, customers are tricked into disclosing personal data by websites that mimic your own for malicious intent. WebHawk proactively shines a flashlight into the corners of the infinite web, running quadrillions of scans 24/7, and using machine learning to identify the hackers at the earliest possible preparation stages.
Complete Managed Services
As an active response team for digital risk, we monitor, manage, block and take down any risks to your customers, taking the entire problem of consumer-facing phishing scams off your hands. We safeguard your assets, protect your customers, remove the threat, and even take action against the attackers, providing ultimate peace of mind.
Zero On-Boarding
WebHawk can be deployed in minutes, and requires zero integration with your system. Lightweight and invisible, your digital assets are continually protected from manipulation and impersonation attempts anywhere on the web.

Long-Term Partner Relationships is in Our Core.
Security Breaches, Data Leaks, and Email-Based Attacks are a real threat for any Organization. Now, more than ever, you need a new approach to cyber security and data management. don't let the limitations of traditional technologies prevent you from protecting data and corporate information.
We have made it our mission to mitigate the risks you face from email, and support you in reducing the cost and complexity of protecting yourself by moving this workload to the cloud. We live and breathe cloud technology. We developed our proprietary cloud architecture to offer you comprehensive email security, service continuity and archiving in a single subscription service. Our goal is to make it easier for you to protect your business in today's fast-changing security and risk environment.
That is why our partner program is designed to do more than support joint new business efforts - we work hard to protect our partners and their customer relationships, and to provide tools to grow their business.
It works. Our partners not only win business, but retain it. Retention rates are running at higher than 95%.
Services
We act as a barrier or protective shield between your computer and the threat of the cyber world. There are many features like - ISP LOAD balancing, Gateway Antivirus, Spam Prevention, MITM Attack prevention, Disk Encryption, Boot Level Encryption, and Monitoring.

MITM Attack Prevention
Webhawk® blocks all MITM attacks like Sniffing, DNS Spoofing, WEB Spoofing, Hijacking, Injection etc. It manages a list with static entries making it an optimal choice in those statically configured networks without DHCP.

Anti Spam
Webhawk® DNS also provide feature of protecting from spamming mails or domains as it can directly block all the domains which leads to unsolicited emails.

Internet Load Balancing
Webhawk® provide an intelligenent load balancing feature to balance network traffic and intelligently distribute the traffice. It prevents from network latancy. It balances traffic load in two ways "BALANCE MODE" and "FAILURE MODE".

Gateway Antivirus
In order to Ensure your network and devices remain free of malware, viruses, trojans, worms, spyware we provides Gateway Antivirus as well. This Antivirus uses advanced, multi-layered threat detection engines to identify and block malware at the network gateway.

Monitoring
Webhawk® dashboard provides Realtime Network Traffic Scanning (RNTS), monitoring and controlling as well as keeping track of the performance of your systems.

OEM Solution
With the help of webhawk oem Admin can manage the clients, resellers, distributers, as well as the clients under the reseller and distribututer.
Content Filtering
Content filtering in Webhawk® act as a shield between the Internet and a end users, blocking access from potentially objectionable or offensive material.
Why choose us?
Safeguard for digital assets of any industries. IT and security teams who work together to defend, respond and recover from disruption demonstrate true resilience.

Industries
Assess your industrial cyber security program requirements. Find vulnerabilities with WebHawk® cyber security risk assessment.
- Control system expertise.
- Proven technologies.
- World-class insight.
- Deep control expertise.
- Automate compliance.

Large Enterprises
A connected world increases the probability that your plant and your operations will be hacked. It's that simple.
Why? Because today's production facilities rely on the same digital technologies that hackers know how to crack. And the severity of threats is increasing.

Micro, Small & Medium Enterprises - MSME
SMEs are the new big target for cyber attacks and see themselves confronted with a large variety of cyber threats.
- Cybercrime: Relentless growth.
- Cybersecurity: Very complex issue for businesses.
- SMEs: New hacker's target.
- New Threats: Cybersecurity risks ranking.
Clients
Licenses
Support Hours
Countries Reached
Recognition







Association




Contact Us
SCO-25, Near Radission Hotel, Zirakpur, SAS Nagar, India - 140603
contact@mymntech.com
+91-788-849-1800
+1-904-297-5651